In a world where data is king, protecting your information on SaaS platforms is crucial. Join us as we delve into the realm of SaaS security and discover how you can fortify your defences against potential breaches.

Software as a Service (SaaS) has revolutionized the way businesses access and use software. Instead of relying on traditional, on-premise systems, companies can now subscribe to software applications that are hosted and maintained by third-party providers. This not only saves time and resources but also allows for greater flexibility and scalability.
However, with this convenience comes new security concerns. As companies move their operations to SaaS platforms, they must also consider how to safeguard their sensitive data from potential threats. In this section, we will explore what exactly SaaS is and why it is crucial for businesses to prioritize data security in these platforms.
Understanding Software as a Service
In simple terms, SaaS is a software distribution model where applications are centrally hosted by a provider and made accessible over the internet through a subscription-based payment plan. This means that instead of purchasing individual licenses for each user or device, businesses pay for the services they need on-demand.
Why Data Security Matters in SaaS Platforms
Data security involves protecting confidential information from unauthorized access or exposure. In today’s digital world, data has become one of the most valuable assets for businesses. From customer information to financial records, organizations store large amounts of sensitive data that must be kept secure at all times.
As more business operations rely on cloud-based solutions like SaaS platforms, it’s paramount that companies prioritize data security measures within these environments. Here are some reasons why data security is crucial in SaaS platforms:
1. Shared Responsibility: Although vendors provide security measures within their platform, it is ultimately up to businesses to ensure their own data remains protected. Due diligence should involve thorough research into the vendor’s security protocols and implementing additional measures if necessary.
2. Phishing attacks: Phishing attacks are one of the most common forms of cybercrime targeting organizations through emails or fake websites designed to obtain sensitive information such as login credentials.
3. Insider threats: While data breaches caused by external actors often make headlines, insider threats pose a significant risk to a company’s data security. Employees or contractors with malicious intent can access and misuse sensitive data if proper controls are not in place.
4. Compliance: Depending on the industry, businesses may be subject to specific compliance and regulatory standards that require them to protect their data appropriately.
Understanding the regulatory landscape for SaaS security and compliance
One of the important aspects of SaaS security is to comply with industry-specific regulations such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), or PCI DSS (Payment Card Industry Data Security Standard).
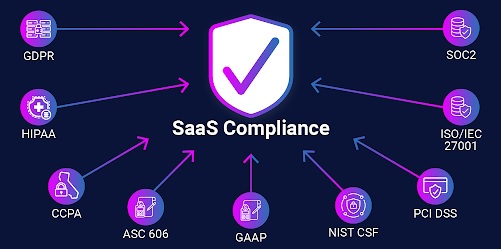
These regulations come with strict requirements for protecting sensitive data from unauthorized access or disclosure. For instance, GDPR requires organizations to implement appropriate technical and organizational measures to protect personal data, while HIPAA mandates healthcare providers to adhere to strict guidelines for safeguarding electronic protected health information. Failure to comply with these regulations can result in severe penalties and damage to an organization’s reputation.
Apart from industry-specific regulations, there are also laws governing data protection at a global level. The most prominent example is the California Consumer Privacy Act (CCPA), which grants state residents the right over their personal information collected by businesses.
This law applies not only to businesses operating in California but also any company that deals with Californian consumers’ data. With more states following suit by enacting similar privacy laws, it has become imperative for organizations using SaaS platforms to understand their obligations regarding compliance.
Understanding the regulatory landscape for SaaS security and compliance is crucial for protecting sensitive data from cyber threats and maintaining trust with customers. This is where partnering with a trusted SaaS security provider can make a significant difference. Such providers have the necessary expertise and tools to help businesses navigate the complex regulatory landscape, ensuring compliance and safeguarding sensitive data.
Common SaaS security challenges:
Common SaaS security challenges can pose a significant threat to businesses of all sizes. As more companies move their operations to the cloud and rely on Software as a Service (SaaS) platforms for their daily operations, they must also be aware of the potential risks associated with this technology. In this section, we will discuss some of the most common SaaS security challenges that businesses face and how they can overcome them.
Lack of Encryption:
Encryption is a process that converts readable text into coded characters which can only be accessed with a specific key or password. When using SaaS platforms for storing sensitive data, lack of encryption leaves that information vulnerable to potential breaches.
To ensure data security on SaaS platforms, it is essential for businesses to use strong encryption protocols while transmitting and storing data on the cloud. Companies can also consider using a data encryption service or a third-party encryption tool to add an extra layer of protection.
Regular Security Audits:
Regular security audits are essential for identifying any potential vulnerabilities in a company’s SaaS applications and infrastructure. These audits involve reviewing security protocols, user access controls, and other security measures to identify any loopholes that could be exploited by cybercriminals.
By conducting regular security audits of their SaaS platforms, businesses can stay one step ahead of potential threats and ensure that their sensitive data is adequately protected.
Data Backup and Recovery in Saas:
When using a Software as a Service (SaaS) platform, one of the key concerns for businesses is the protection and recovery of their valuable data. With data breaches becoming more common and regulations like the General Data Protection Regulation (GDPR) holding companies accountable for safeguarding customer information, having a robust data backup and recovery plan in place has become crucial.
In SaaS platforms, data backups are typically done automatically by the service provider through various methods such as snapshots, cloning, replication, etc. These backups are stored in secure off-site locations to ensure that they are not affected by any issues with the primary servers.
It’s also essential for SaaS providers to have rigorous testing procedures in place for their disaster recovery plans to identify any potential flaws and make necessary improvements before an actual emergency occurs.
Data encryption is another critical component when it comes to protecting sensitive information during back up processes. Encryption ensures that even if attackers gain access to the backed-up data, they won’t be able to read or use it without the decryption key.
Having robust data backup and recovery protocols in place is vital when using a SaaS platform. Businesses should also make sure to choose a reputable and reliable provider that prioritizes data security and regularly updates their measures to stay compliant with industry regulations. By doing so, businesses can minimize the risks of losing valuable data and maintain trust with their customers.
Data Privacy Features in Saas:
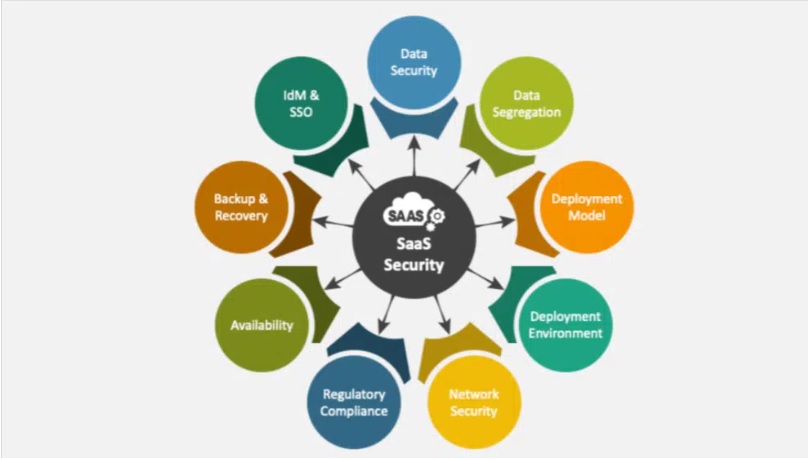
When it comes to using SaaS for your business, data privacy is of utmost importance. Data privacy features in SaaS can be described as the tools and controls that ensure the protection and confidentiality of sensitive information stored and processed by a SaaS application. These features are designed to protect against any unauthorized access, use, or disclosure of personal or confidential data.
One of the key data privacy features in SaaS is encryption. This involves converting plain text into code, making it unreadable without a specific key or password. With encryption, even if there is a security breach, hackers won’t be able to obtain any valuable information from the encrypted data.
Another essential feature is multi-factor authentication (MFA). MFA requires users to provide more than one form of identification before gaining access to the system. It adds an extra layer of security, making it difficult for unauthorized individuals to gain access to sensitive data.
Role-based access control (RBAC) is also an important feature when it comes to data privacy in SaaS. RBAC ensures that only authorized personnel have access to specific data based on their roles within an organization. This helps prevent accidental leaks or misuse of sensitive information by limiting who can view, edit, or delete certain types of data.
Data masking is another vital feature for protecting confidential information in SaaS applications. It involves hiding sensitive parts of the data while keeping its original format intact so that only authorized personnel can see full details.
In addition to these technical measures, many reputable SaaS providers offer compliance certifications such as SOC 2 Type II and ISO 27001 which demonstrate their commitment towards maintaining high levels of security and meeting industry standards for protecting customer’s private information.
Choosing a SaaS provider that prioritizes data privacy and offers robust features such as encryption, MFA, RBAC, data masking, and compliance certifications is vital for ensuring the security of your business’s sensitive information. It not only protects you from potential data breaches but also helps maintain trust with your customers by assuring them that their private information is in safe hands.
Security by Design in Saas:
Security by design is a development approach that prioritizes the integration of security measures in every stage of the product life cycle. In SaaS, this means implementing security measures from the design phase to deployment and maintenance. Security by design ensures that potential vulnerabilities are addressed proactively, rather than being added as an afterthought.
In traditional software development, security is often seen as an additional feature or add-on that is implemented at the end of the development process. However, with SaaS, continuous updates and changes are made to the software through a cloud-based model, making it more susceptible to attacks. This makes security by design critical in ensuring data safety and compliance.
The first step towards incorporating security by design in SaaS is conducting thorough risk assessments during the initial stages of development. This involves identifying potential threats and vulnerabilities specific to your SaaS product and its target market. It also includes evaluating how sensitive data will be processed, stored, and transmitted within your system.
Based on these identified risks, developers can then implement appropriate controls and countermeasures to mitigate them. These may include encryption techniques, access controls for user authentication, secure coding practices, regular vulnerability scans, and frequent penetration testing.
Another crucial aspect of implementing security by design is ensuring all third-party integrations meet strict security standards. As SaaS platforms typically rely on various APIs (Application Programming Interfaces) to function seamlessly with other systems or applications, any potential weaknesses in these integrations can pose significant threats if not adequately secured.
Moreover, regular code reviews throughout the software development life cycle are vital for identifying any new vulnerabilities or weaknesses introduced within existing codes during updates or modifications.
By proactively integrating data protection measures into their products’ core architecture rather than adding them as an afterthought, SaaS providers can ensure compliance with these regulations and gain the trust of their customers.
Security by design is a critical aspect of ensuring data security and compliance in SaaS products. By implementing security measures from the initial stages of development, continuously reviewing and updating them throughout the product’s life cycle, and ensuring all third-party integrations meet strict security standards, SaaS providers can build a robust and secure platform that instills confidence in their users’ data protection.
Continuous Monitoring and Incident Response in Saas:
Continuous monitoring and incident response are essential components of data security and compliance in SaaS. As businesses increasingly rely on cloud-based services for their operations, it becomes crucial to have a robust system in place that constantly monitors for potential threats and responds swiftly to any incidents.
The first step in ensuring continuous monitoring is to implement a robust security infrastructure. This includes, but is not limited to, firewalls, intrusion detection systems, antivirus software, and secure servers. These tools work together to establish a strong perimeter defence against cyberattacks.
In addition to these measures, regular vulnerability scans should be conducted to identify any weaknesses in the system. These scans can help detect any potential threats or points of entry that may have been missed during the initial setup of the security infrastructure.
But having a strong defence system is only one aspect of continuous monitoring. The key lies in actively monitoring network traffic and logs for any anomalies or suspicious activities. This requires constant vigilance and often utilizes automated systems such as Security Information and Event Management (SIEM) tools. SIEM tools collect and analyse data from various sources within the network, providing real-time insights into potential threats or breaches.
In case an incident does occur, a well-defined incident response plan must be in place to minimize damage and mitigate risks promptly. This includes identifying the nature of the incident, containing it before it spreads further, conducting forensic analysis to determine its cause, notifying relevant parties such as customers or authorities (if necessary), and restoring normal operations as soon as possible.
Having a detailed incident response plan ready beforehand minimizes confusion during high-stress situations and enables organizations to act swiftly while also adhering to compliance regulations.
Continuous monitoring paired with an efficient incident response plan work hand-in-hand towards maintaining data security in SaaS environments. By regularly scanning for vulnerabilities and actively monitoring network traffic coupled with swift responses during incidents – businesses can ensure maximum protection against cyber threats while complying with industry regulations.
User Education and Training for Data security in Saas:
User education and training play a crucial role in ensuring data security and compliance in SaaS (Software as a Service) environments. With the increasing use of cloud-based software, it has become essential for organizations to educate their users on best practices for protecting sensitive information and complying with relevant regulations.
The first step to effective user education is creating awareness about the potential risks associated with data breaches. This includes educating users on common tactics used by cybercriminals, such as phishing scams or social engineering, which can compromise their login credentials or lead them to disclose sensitive information.
Another important aspect of user education is providing training on how to identify and handle sensitive data. Users should be aware of what constitutes personal or confidential information and how they should handle it in accordance with compliance guidelines. This could include policies around encryption, access control, or specific requirements for different types of data.
Users must also be trained on how to securely access SaaS applications. This may involve implementing multi-factor authentication measures or using secure virtual private networks when accessing company data remotely.
In addition to general cybersecurity training, specific training related to the SaaS environment should also be provided. Users need to understand how the application works and what security features are available, such as data backups and audit logs. They should also be educated on any limitations regarding user responsibilities for securing their own access within the SaaS platform.
Regularly scheduled refresher courses are essential for keeping users up-to-date with new threats or changes in compliance regulations that may impact their use of SaaS applications. These courses can help reinforce knowledge and awareness among users, ultimately reducing the risk of human error leading to data breaches.
Furthermore, organizations must provide clear guidelines and procedures for reporting suspicious activities or potential incidents. Employees should know who to contact if they suspect a breach has occurred so that prompt action can be taken to mitigate any damage.
User education and training are critical components of ensuring data security and compliance in SaaS environments. Organizations must invest in developing a comprehensive education and training program that addresses both general cybersecurity practices and specific guidelines for using SaaS applications securely. By doing so, businesses can minimize their risk of data breaches and maintain compliance with relevant regulations.